Manage record access policies
Overview
Each policy consists of its details (name, description, and status), rules, and change history. This page covers how to create and delete a policy, and how to edit the policy’s details.
For information on how to view, add, edit, or delete policy rules, see Manage record access policy rules. See the Record access policies page for details about the change history.
Policies can also be created and managed via the API. See the the Skedulo API Reference Guide and developer guide for more information.
Create a record access policy
You can create a policy in the web app by doing one of the following:
- Create a policy from a template and use it as is.
- Create a policy from a template and edit the rules to customize the policy for a specific use case.
- Create a policy from blank and define the rules from scratch.
Policies are created with a status of Disabled by default. The policy and its rules will take effect after the policy has been Enabled. This gives administrators the ability to build and configure new policies before they are activated across the system for all users.
Create a new record access policy from a template
To create a record access policy from a template, do the following:
- On the Settings > Record access policies page, click Create Policy. The Create a new record access policy dialog displays.
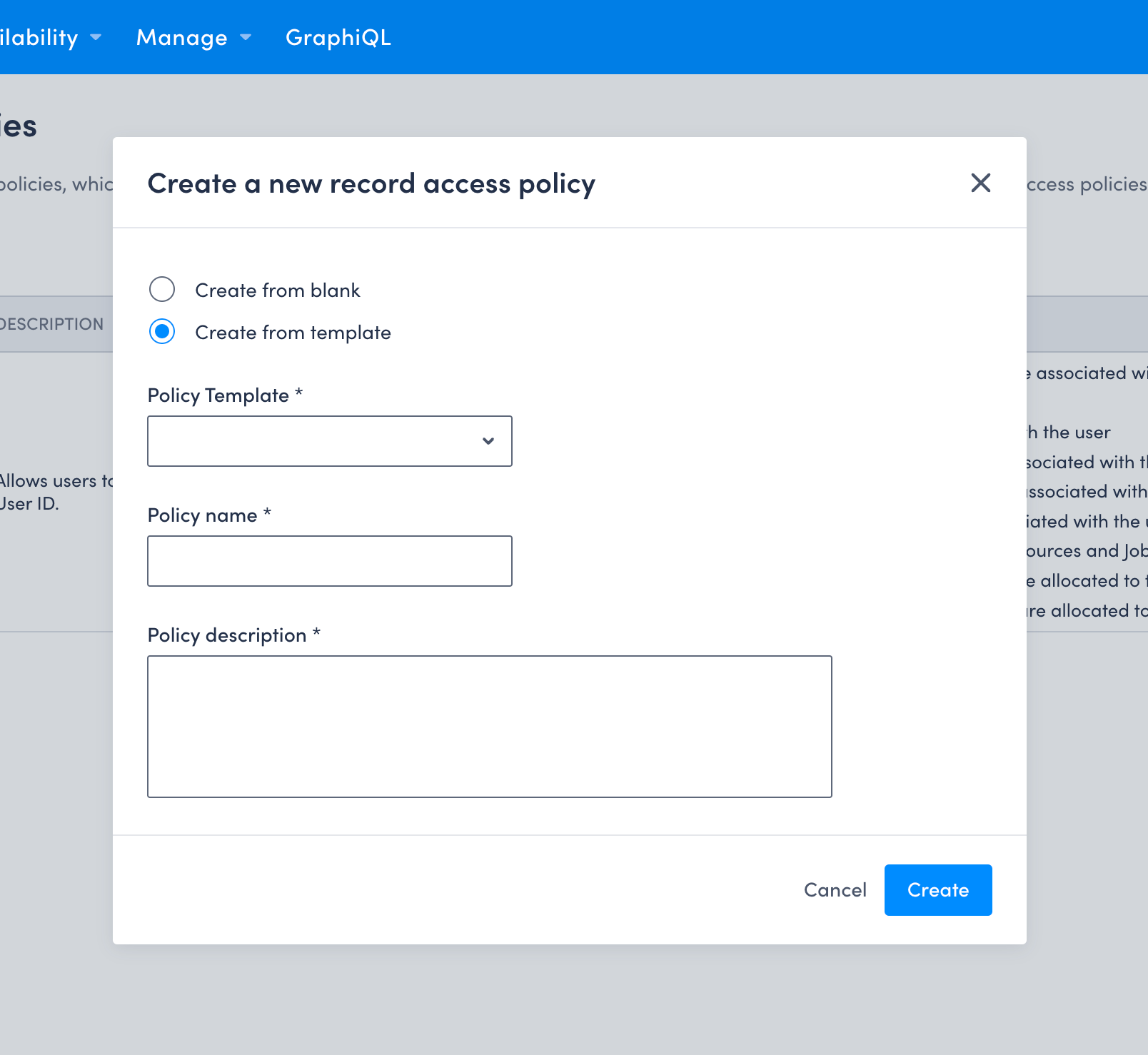
- Click Create from template and then click to select a template from the Policy template drop-down.
- Provide a Policy name and Policy description for the new policy.
- Click Create to save your changes and create the policy. The new policy’s details page displays.
When creating a policy from a template, the associated filtering rules will automatically be created with it.
Create a new record access policy from blank
To create a record access policy from blank, do the following:
- On the Settings > Record access policies page, click Create Policy. The Create a new record access policy dialog displays with Create from blank selected by default.
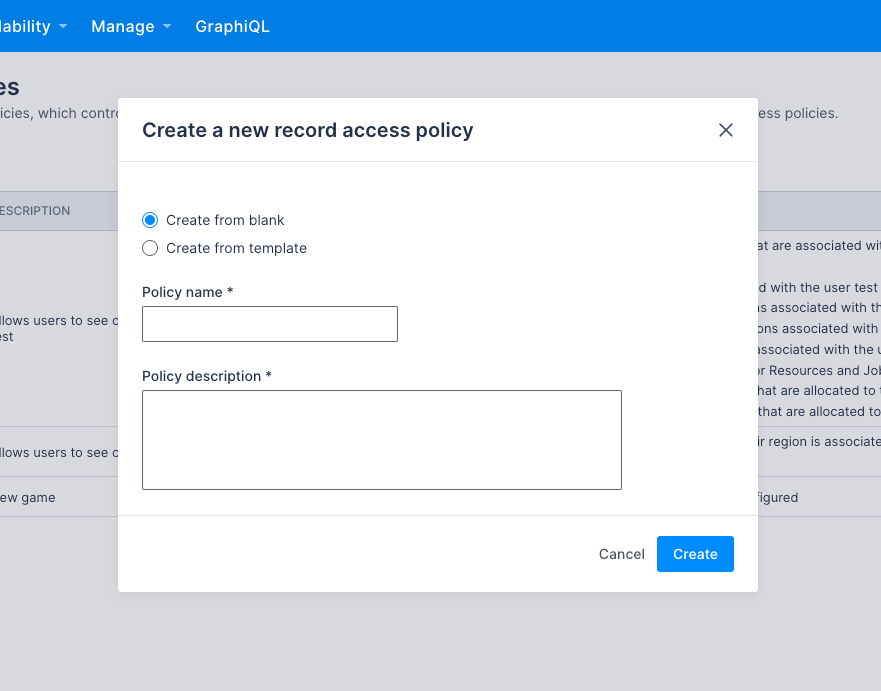
- Provide a Policy name and Policy description for the new policy.
- Click Create to save your changes and create the policy. The new policy’s details page displays.
Enable a record access policy
To enable a record access policy, do the following:
- On the Settings > Record access policies page, click the name of the record access policy you want to enable. The policy details page displays.
- Under Status, click Enabled and then click Save.
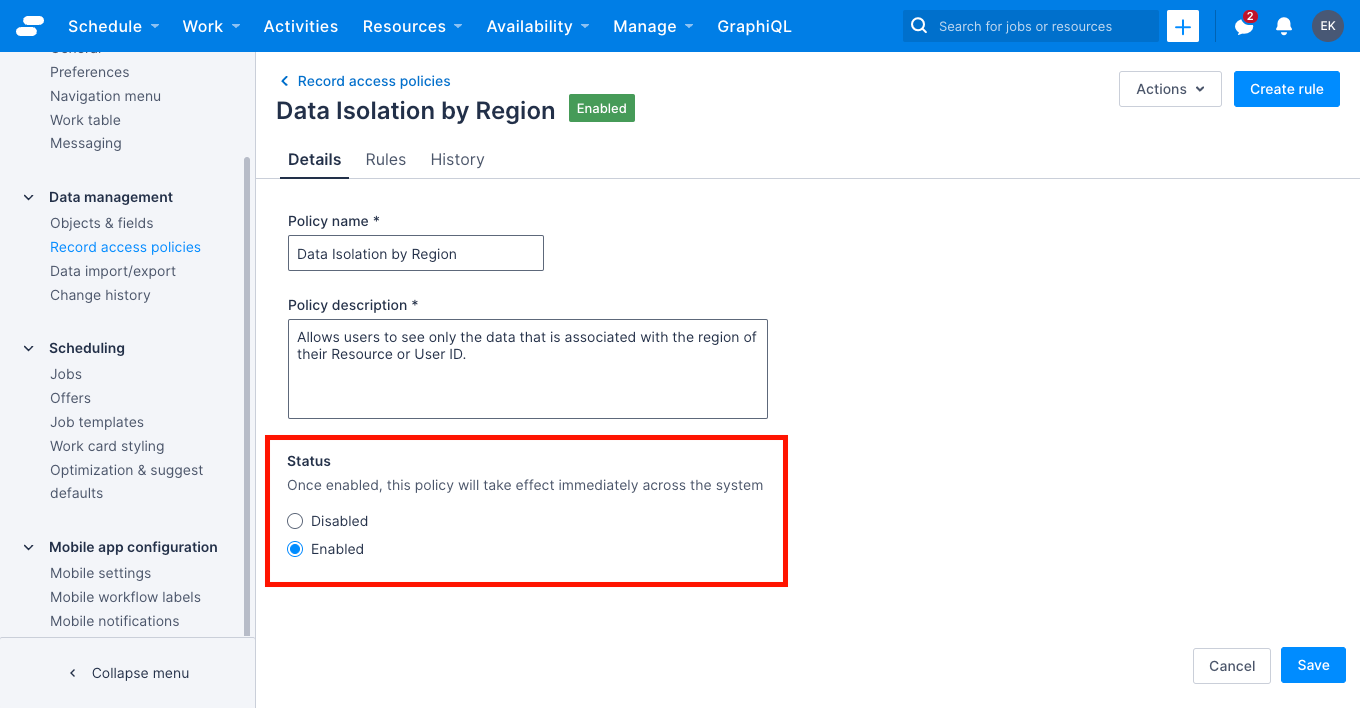
Once enabled, the policy and its rules take effect across the system immediately.
To disable a policy, follow the same process, but select Disable and then Save instead.
Edit a record access policy’s details
To edit the details of an existing policy, do the following:
- On the Settings > Record access policies page, click the name of the record access policy you want to edit. The policy details page displays.
- Make changes to the Policy name, Policy description, or Status fields.
- Click Save. Success notification displays.
Delete a policy
To delete one or more policies, do the following:
- On the Settings > Record access policies page, click the checkbox next to the name of the record access policy, or policies, you want to delete. The Delete and Deselect All options appear.
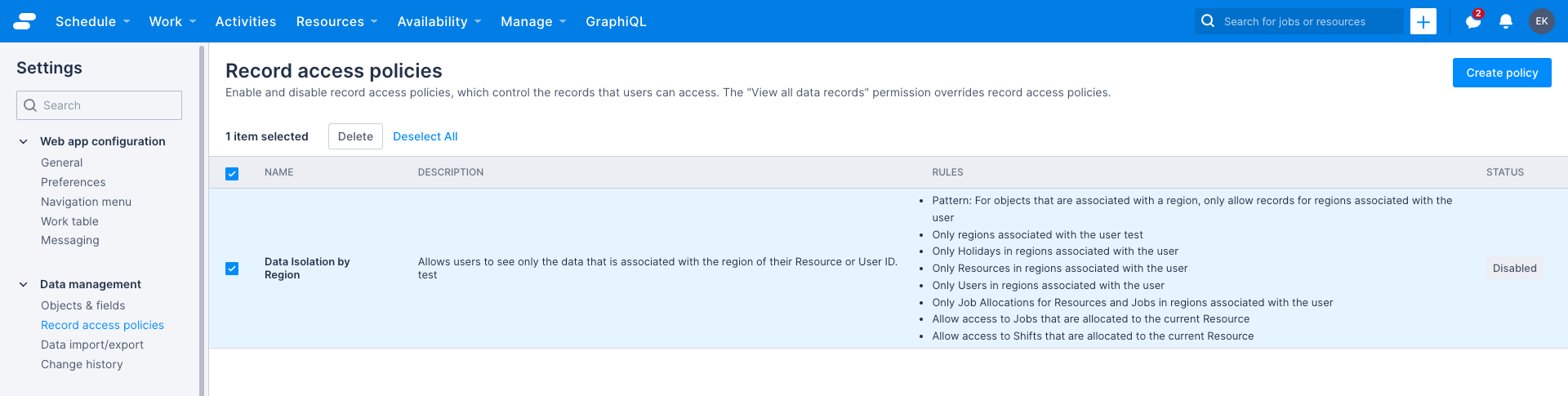
- Click Delete.
- To confirm the deletion, click Yes, or click Cancel to return to the policy list without deleting.
Note
Deleting a policy cannot be reversed, so this action should be taken with due care. If you are unsure whether a policy will be needed in future, rather disable it.Apply a policy to a subset of users
Record access policies only allow excluding a rule based on a user having a role or permission, rather than applying a rule to a user, permission, or role. This is configured as part of each rule in the policy.
The reason for this is so that the general principle of roles and permissions, that assigning a role or permission to a user should never reduce their access or capabilities, is upheld. This allows roles and permissions to be combined together in a sensible and predictable way.
If a policy should only apply to some users, then the role or roles (or specific permissions) that apply to all other users must be excluded from each rule in the policy. For example, if a policy must only apply to resources, but not schedulers, then the rules in the policy must be configured to exclude the Scheduler role.
Feedback
Was this page helpful?