Record access policies
Overview
Record access policies allow administrators to create filtering rules that get applied whenever data is requested via the web app, mobile app, or APIs. Record access policy rules filter the data that is returned for any given request.
Record access policies provide flexible fine-grained control over the data that each user can see based on a set of rules and conditions that are customized for specific use-cases. A single policy can consist of multiple rules; each with its own filter that specifies how an object’s data should be available in the team.
Important
Record access policies are only available on the Skedulo Pulse Platform.Use case examples
Skedulo provides policy templates for the most common use cases, for example, there is a policy template for enforcing region isolation of your Skedulo data, such that users only see data records that belong to the region or regions with which they are associated. See the templates section for more information about this template.
Other applications of record access policies could include, but are not limited to, the following scenarios:
- Users with a specific role (for example, a hypothetical role called “Installers”) must only be able to see jobs with a certain job type (for example, job types named “Installation”).
- Users that are linked to a specific entity (a custom object for a provider or supplier, for example) are only able to view account records that are also linked to that object.
- Users must only be able to view jobs that they are allocated to and not any others.
- Users must only have access to a record under certain conditions, for example, a user may only see a contact when they are allocated to a job to which the contact is also linked.
Permission requirements
Only users with the Administrator role or with a role containing the Modify record access policies permission are able to create and manage record access policies.
Users with the Administrator role are automatically exempt from any record access policies and will always see all data from a Skedulo instance.
Access record access policies
To view and manage record access policies, do the following:
- Navigate to Settings > Data management > Record access policies.
The Record access policies page lists any existing record access policies that have been added to your Skedulo instance. Each policy shows a summary of its rules and its status (enabled or disabled).
From this page, you can perform the following actions:
- Navigate to the policy details page where configuration changes can be made (more information follows below).
- Create a new policy.
- Delete policies.
See Manage record access policies for more information on creating and deleting policies.
View a record access policy’s details
To view a policy’s details and access additional functionality pertaining to the policy, do the following:
- Click the name of policy you want to view. The policy details page displays on the Details tab.
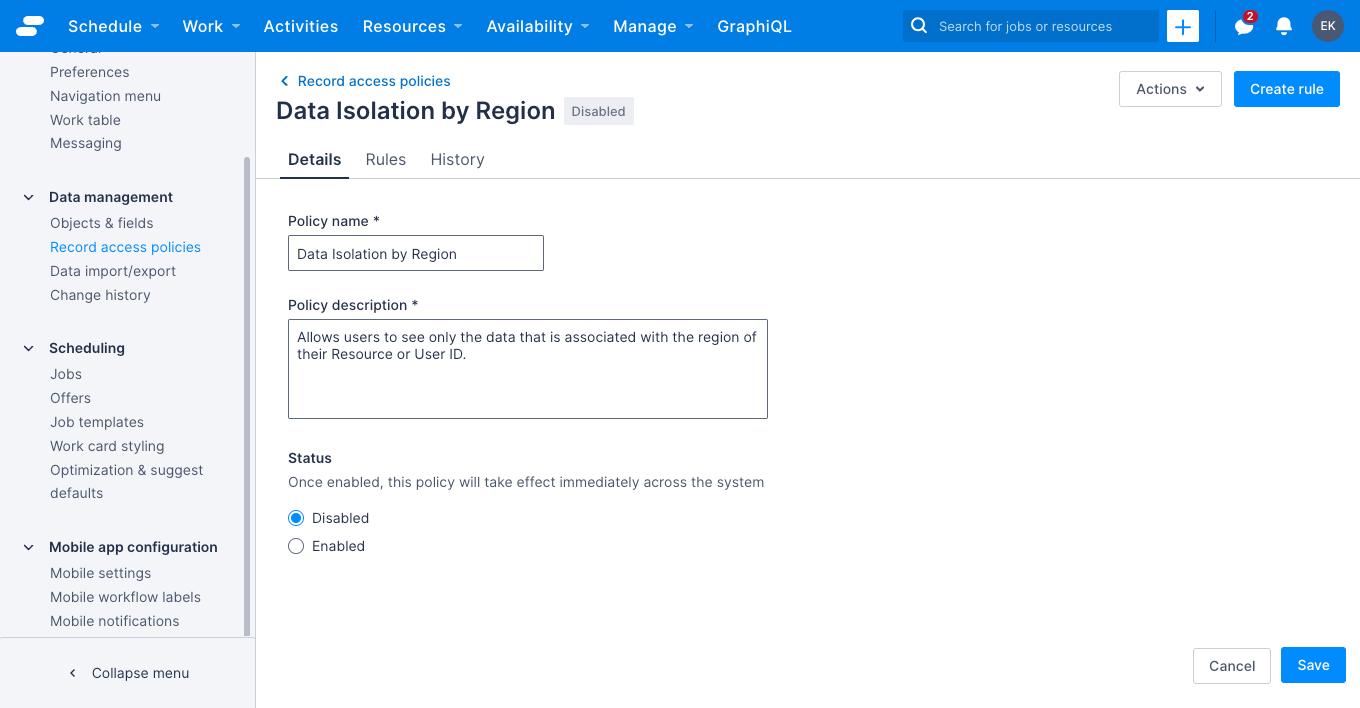
From the policy details page, you can do the following:
- Make changes to the policy details and status. See Manage record access policies for more information.
- View and manage the policy rules. See Manage record access policy rules for more information.
- View the change history for the policy (more information follows below).
View the policy’s change history
To see a list of changes that have been made to the policy, do the following:
- On the policy details page, click the History tab. A list of changes displays.
The History tab shows when a change occurred, a summary of the change, and the user who performed the change. Additional information about a change can be viewed by clicking Columns and then selecting Raw change data. This column shows the state of the data following the change that it is associated with.
Note that a summary of changes to individual rules is not shown in the CHANGE column and details can instead be observed in the RAW CHANGE DATA column.
Limits and limitations
- A maximum of 10 policies, each with up to 20 rules, can be configured per team.
- Record access policies are only available on the Skedulo Pulse Platform.
- Temporary regions are not supported.
- Time and date-based filters are not supported.
CreatedByandLastModifiedBylookups are excluded from record access policies, meaning that if a query traverses that relationship it will be able to retrieve all of the user details (even if they would not be able to see that user normally).- Record access policies do not apply to data that are not part of the tenant’s data model or in systems that use a copy of the tenant’s data, for example in the change history pages and rule conflicts console. Note that they do apply to custom objects and fields that are added to the tenant’s data model.
- Record access policies do not apply to data from Custom forms.
Important
Policy rules are extremely flexible, but can also cause the Skedulo web or mobile app to stop functioning properly if configured incorrectly. We recommend that you test new policies and their rules in a separate environment before applying them to your production system.Feedback
Was this page helpful?